Log4j2 security vulnerability and workaround

Published on 09 Dec 2021 by Lekro, TraksAG
Edit: Mojang has posted an official announcement regarding this issue, be sure to check it out! You can find the announcement here. In case you’re interested in the technical details, the exploit is officially known as CVE-2021-44228, which you can use as a search term.
We’ve become aware of a security vulnerability affecting both minecraft clients and servers. This is a serious vulnerability. In essence, the exploit works by sending special messages in chat. These messages force your computer to connect to a malicious computer. Please follow the instructions in this blog post to work around the issue for your Minecraft client.
We’ve figured out the following:
- If you’re running Minecraft on Java 8, we believe the exploit allows anyone to run arbitrary code on your computer.
- If you’re running Minecraft on Java 16 and above (which is the case if you’re on Minecraft 1.16 and above), this exploit allows anyone to crash your client, or log your IP address (we actually reproduced these).
We’ve worked around this on CK, so the CK machine isn’t affected by the exploit. However, it is still important that you fix it on your end, so the exploit doesn’t happen on your computer. Fortunately it’s not that hard. Some of y’all have probably heard of this already, and here is how to work around it.
Working around the vulnerability
Please note that this fix only works for Minecraft 1.17 and above. The basic idea is to add the following “Java argument” to your client:
-Dlog4j2.formatMsgNoLookups=true
Here is how to do that on various launchers:
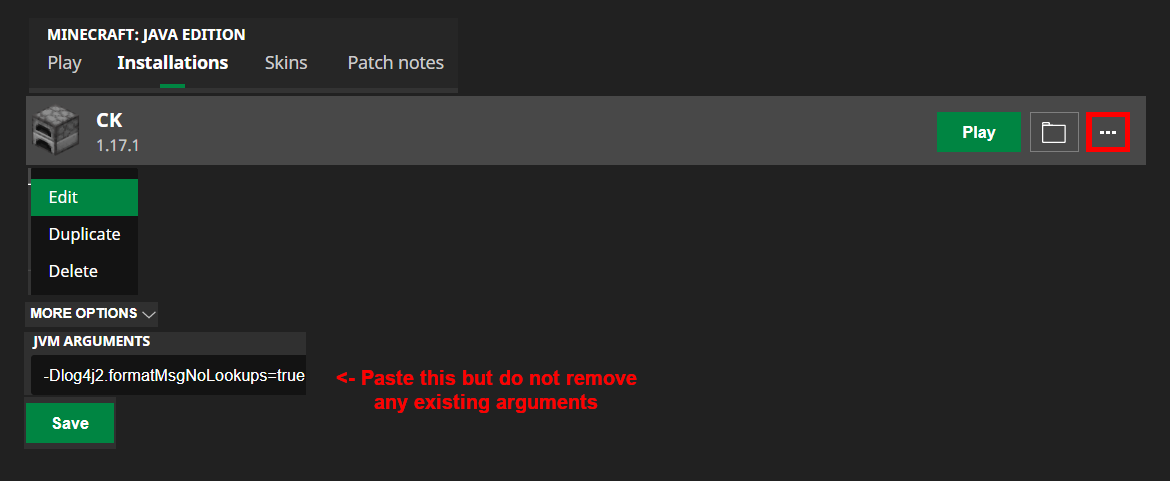
Vanilla launcher
Go to your “Installations”, click on the profile you’re using, click on “More options”, then add
-Dlog4j2.formatMsgNoLookups=true
to the JVM arguments.
(click to view larger version)
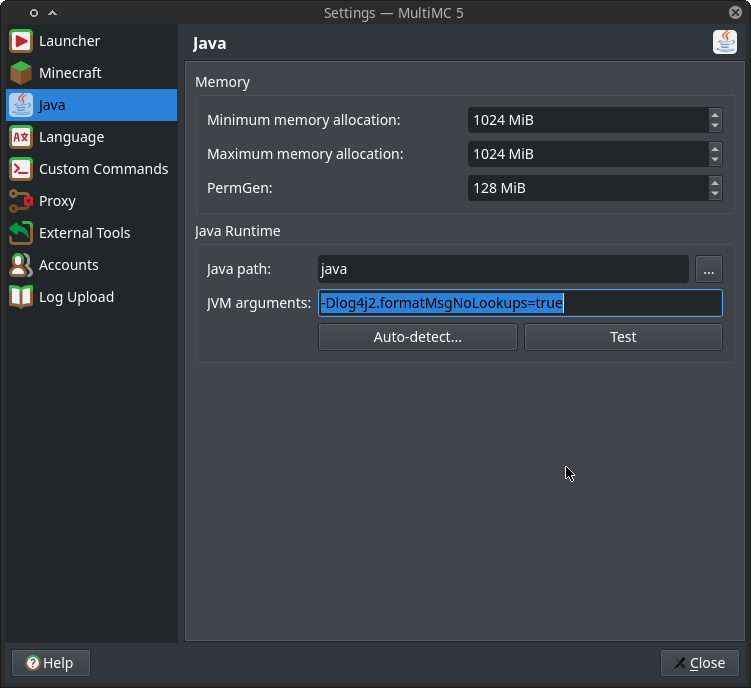
MultiMC
Click “Settings” and then go to the “Java” tab, and write
-Dlog4j2.formatMsgNoLookups=true
in the Java arguments.
(click to view larger version)
Subscribe
Subscribe to this blog via RSS.
Categories
Recent Posts

Powered by Velocity
community, 05 Oct 2025
1.21.4 is live on C...
community, 11 May 2025
1.21.1 is live on C...
community, 23 Oct 2024

Migrating to a new ...
developer, 23 Oct 2024
Popular Tags
server (15) update (11) discord (2) backend (1) skyblock (1) website (1)